11. Fake Apps

Always download apps from trusted stores as fake apps gain access to your confidential financial information and use it for unauthorized transactions.
12. They Get Duplicate SIM Card To Get OTP

Criminals contact your mobile operator with fake identity proof and get a duplicate SIM card. The operator deactivates your original SIM and the criminal generates a one-time password (OTP) on the phone to conduct online transactions.
13. Vishing
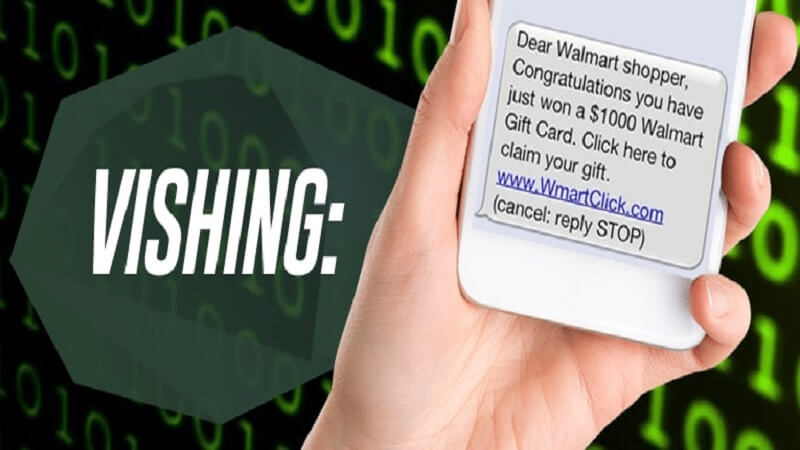
Through a mobile phone using SMS or phone calls, criminals trick you into revealing your password, PIN or account number.
14. They Make New Cards

Using the personal information that is stolen from application forms, lost or discarded documents, cybercriminals make new cards.
15. Lost Or Stolen Cards Interception

Criminals carry out transactions using stolen cards, those intercepted by mail before they reach the owner from the issuer, or by fishing out information like PINs and passwords from trash bins.
Did you face any issue with the online transaction so far? How did you solve it? If you know any other way that is not mentioned here, share us in the comments. Look out for this fake SMS from Jio Tv which steals your credit card details – beware!














